The connected world as we know it, with remote work and cloud computing, is too new for us to appreciate the amazing ability to control a computer remotely. But if we think back a generation or two, that concept was pretty wild. Next comes Telnet – the original technology that started the remote access movement.
If you are new to networking or just interested in how We built internet tooling in the early years, read on. We will reveal what Telnet is, fun historical facts, the reasons it is still used for some applications, how it works in many cases, high-level commands to use it and advantages of it. By the end of this blog, you will be ready to understand Telnet and we will do it in layman’s terms. Let’s jump in!
What is Telnet?
Essentially, Telnet is a network protocol that allows users to make a remote connection to another computer or device over a network and communicate with it. Telnet means “Teletype Network,” and it serves as a virtual terminal that lets you log in to a remote system as if you are sitting in front of it. That is, you can type commands on your laptop that runs on a server halfway around the globe. This is Telnet.
Telnet uses a client/server architecture, in which the “client” is the software on your device that establishes the session, and the “server” is the remote computer that accepts the session. Once the session has been established, you are now able to execute commands, transfer files, or manage configurations through a text-based user interface. As a client/server technology, Telnet is bidirectional and interactive, which means you are sending inputs and receiving output all at the same time.
While graphical remote tools are available such as Remote Desktop, Telnet is completely text-based, making it lightweight and efficient for use with command-line applications. Telnet does, however, send data in plain-text, which can be problematic from a security standpoint, but we will get into that later. Think of Telnet on a beginner’s level equivalently to a phone call: direct, uncomplicated, and not encrypted.
The History of Telnet: From ARPANET to Internet Essential
The history of Telnet starts in the late 1960s at the beginning of computer networking. It was developed as a function under the ARPA project, which funded the original internet, known as ARPANET, by the Department of Defense. In 1969 the researchers were looking for a way to connect terminals to computers on this experimental network: thus, Telnet was born. This was at a time when computers were enormous mainframes, and being able to share resources at a distance changed everything in terms of collaborative work.
The protocol was not established at that time; in fact, it was an ad-hoc method of communication without standards. The first demonstration of Telnet was done in 1969 on the ARPA network, demonstrating remote login from one system to another. By 1971, there were some early specifications of Telnet listed in the RFCs, including RFC 97 – one of the earliest definitions. Telnet grew to support community input through the Internet Engineering Task Force (IETF).
The year 1983 saw the completion of RFC 854, which is a full Telnet Protocol Specification. This established the framework to standardise Telnet as an internet protocol so that it could be implemented in different systems effectively. Telnet developed alongside TCP/IP and it became one of the first application-layer protocols of the OSI model.
By the 1980s and 1990s, Telnet was commonly adopted for remote administration, particularly in Unix environments and early internet environments.
However, with security dilemmas arising contemporaneously with the development of the internet, Telnet began to give way and be overshadowed by alternatives like SSH (Secure Shell) by the late 1990s. Today, Telnet is usually seen as legacy but we still think about the concept of remote access today because of its initial invention.
Why is Telnet Used?
Although Telnet is an older technology, it fills some outlier circumstances where simplicity is better than complexity. In particular, Telnet is used for remote logins and command sessions on servers, routers, switches, and other network devices. System administrators will use it in their jobs to troubleshoot, configure hardware, or monitor processes without being physically front of the machine.
For example, in networking education and the case of legacy systems, one might use Telnet to check whether a specific port is open or whether the server is responding, such checking the web server on port 80. In the early days of the internet and public devices, Telnet was also used for services like weather services and bulletin boards. Even IoT devices or embedded systems can use Telnet if the devices are limited in resources. Telnet is lightweight and has little overhead in processing commands.
However, the modern use of Telnet is limited because of the outdated and insecure protocol itself. Many organisations disable Telnet because protocols such as SSH and SSL offer secure connections. That said, Telnet is still taught in IT courses because understanding Telnet use and limitations provide useful foundational knowledge and complement to more sophisticated tools.
If you are new learning networking is a good place to start, once you understand how Telnet works, you can build complexity with SSH.
How Telnet Functions Analytically
Let’s analyse what happens when a user connects using Telnet without getting too technical. Telnet operates over the TCP/IP suite, using TCP as the connection-oriented protocol. It uses port 23 by default on the server side.
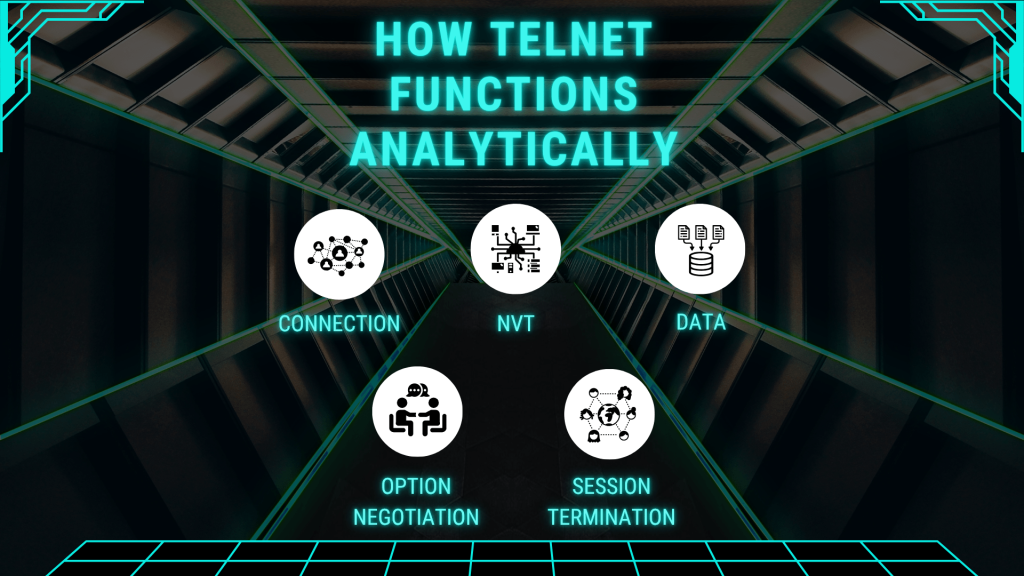
The following is what happens:
1. Connection: The user device (the client) requests a connection to a server using port 23 on the server machine’s Internet Protocol address, TCP then goes through the three-way handshake to establish a connection (SYN, SYN-ACK, ACK). The connection can be considered complete when the session is initialised with a virtual terminal. 
2. NVT: Telnet establishes the concept of NVT, which is a “virtual” terminal that allows two computers with potential different environments to communicate. For example, if the user device uses ASCII characters and the server uses EBCDIC characters, the NVT layer translates as necessary. It also takes care of standardised control characters such as line feeds or carriage returns.
3. Data: All information sent between the client and server is sent as plain text. When the user types a command into the terminal interface, it will be sent to the server as bytes over the network, then interpreted and run on the server, then the output will be sent back to the client for display. Again, to the user, it feels like a transactional and interactive session, like chatting.
4. Option Negotiation: At the beginning of the session, the client and the server negotiate their options using IAC (Interpret as Command) bytes. This will enable the use of certain features such as echo (displaying what has been typed) or specifying window size. For example, the server might say “WILL ECHO,” while the client would respond “DO ECHO” to acknowledge agreement. 
5. Session termination: After all is done, you log off, and the connection is gracefully closed.
Behind the scenes, Telnet is unencrypted plaintext data, which means anyone capturing the network traffic is able to see usernames, passwords and all data being transferred. Because of this, Telnet is often considered insecure for use on public networks. As a learning exercise, using Telnet in a controlled setting such as connecting to a Raspberry Pi, is a way to experience Telnet in a safe way.
Telnet Configuration and Usage Instructions
Telnet is a simple program to use, but the configuration portion is different by operating system. Here we will briefly cover the basics of getting ready to use Telnet, and some basic commands, in a way that is simple and not too technical. For example, let’s keep things beginner friendly and do it from the perspective of Windows, Linux, or routers.
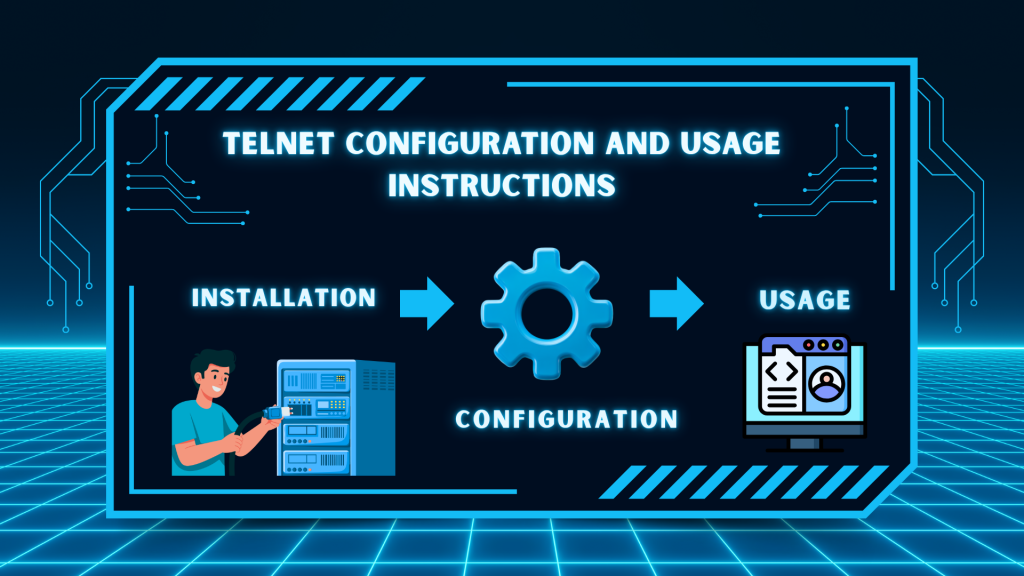
Enabling Telnet
• On Windows: Telnet is not enabled by default on Windows. As a first step, go to the control panel > programs > turn Windows features on or off, and select “Telnet Client” (and “Telnet Server” if you are going to host one). Second, In a command window, type telnet host port.
• On Linux Ubuntu: Install the Telnet client using sudo apt install telnet or the server using sudo apt install telnetd. Once installed, you can start the server with sudo systemctl start inetd.
• On Cisco routers: First, enter privileged mode (enable) and then config mode (configure terminal). Then use line vty 0 4 to set virtual terminal lines, and transport input telnet to allow Telnet access.
The Commands for Use
Once you have established a connection (for example, you have used the command telnet 192.168.1.1), you are now within a session. At this point, you will utilise the key commands (which are all obtainable by pressing Ctrl+] and entering the Telnet prompt);
• open host [port]: to connect to a server (open example.com 23 for example),
• close: to close the current session,
• quit: to quit the Telnet client completely,
• status: to provide connection information,
• mode character/line: to change from character-at-a-time or line-by-line input,
• set echo: toggle echo of what you type back to you locally. 
Within a router config, the command show running-config, indicates viewing your current settings, or the use of the command password telnet creates a password for logging into Telnet. Please be sure to use credentials that cannot easily be guessed or cracked!
For testing use of Telnet: try using telnet towel.blinkenlights.nl to see a fun animation of Star Wars, a great example for beginners.
Benefits of Telnet
Telnet’s ongoing relevance stems from its benefits, particularly for some cases:
1. Simplicity and Ease of Use: No complicated installations, just a simple client and server. Ideal for providing temporary remote access without installing specific software.
2. Compatibility Across Platforms: Functionality across all systems, from a 30-year-old mainframe to a modern device. A helpful capability for legacy situations.
3. Low Resource Overhead: A lightweight protocol makes it fast, especially for low-power devices or slow networks.
4. Unlimited Remote Access: Following a successful login, you will have complete command-line access; ideal for administering networks or servers remotely.
5. Educational Value: A great tool for learning the basics of networking as the nature of the connection allows you to study protocols without the complication of encryption.
6. Port Testing and Debugging: Quickly test and check if a port is an open port for diagnostic purposes, such as for an HTTP or SMTP connection.
Though these benefits are extremely valuable in a controlled environment, keep in mind that the inherent insecurity of Telnet limits its use in today’s world .
Conclusion: The Future of Telnet in a Secure World
Telnet arose during the times of innovation with ARPANET in 1969 that changed remote computing as it gave people more ways to access resources across networks. From its early development as an experimental protocol to an established standard in the 1980’s – Telnet served as a foundational technology for the connected world that we experience today.
We looked into its mechanics – client to server interactions on TCP port 23, its use case in both administration and testing, simple instructions to configure and use Telnet, and we looked at benefits that could be useful, like its simplicity and low overhead.
For those starting out in networking, Telnet is a familiar experience that can introduce a lot of future concepts to you without too much complexity. For the time being, and in our world of security, it is mostly replaced by the Secure Shell (SSH) protocol, which gives you encrypted access so that no one can read what you are sending. If you pursue a career in IT, we suggested some unique ideas for how to play with Telnet, but only in a secure local lab and never in the actual environment.
Telnet has a great deal of history in technology to remind us of what we have accomplished and how now-a-days all we think about is security. Regardless if you are a student, hobby, or professional, having Telnet in your back pocket will help you understand technology better! Happy networking!
Telnet may have been one of the earliest remote access protocols, but understanding its foundation helps you appreciate how far network technologies have evolved today. If you’re passionate about learning networking in-depth and building a rewarding career, explore our trending and job-guarantee courses here.
📲 Stay Updated: Join our WhatsApp Channel for the latest updates, placement news, and events.
▶️ Get Inspired: Check out Video testimonials on our YouTube Channel.
📞 Need Guidance? Talk to our expert education advisors at 1800-313-2545 or WhatsApp at +917840018889 and take your first step towards becoming a networking professional.